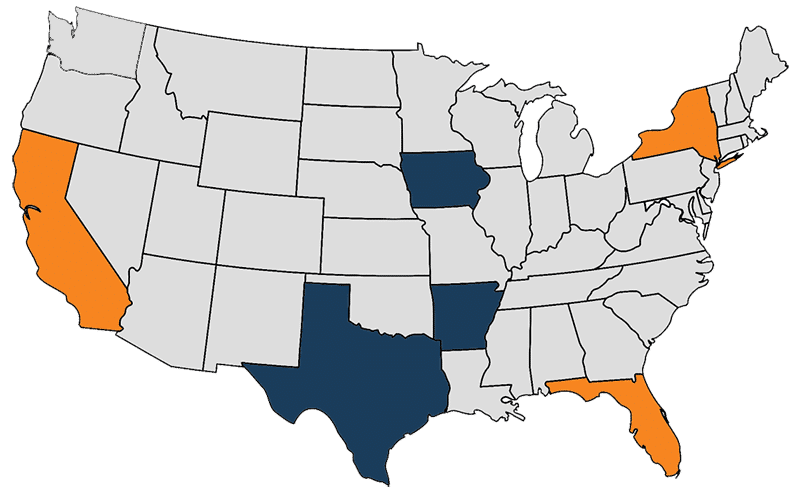
Major Data Breaches of Q2

Today, we take a look at the most noteworthy data breaches that have happened so far in 2019. Visit our blog to see more about how to secure your data.
Watch Out for the One Percent

No IT security is infallible, is your organization prepared for the threats that can sneak in past your security?
What Does a Database Management System Do, Exactly?

The databases your company relies on wouldn’t be as effective without a database management platform.
Redundancy is Everything in a Disaster

For World Backup Day, we decided to discuss just how important having a data backup plan is, and how the definition of disaster is not always cut and dry.
How Microsoft’s Modern Office Provides Data Loss Prevention

Discover the importance of data loss prevention (DLP) policies when it comes to your business’s sensitive information!