Staying Vigilant in the Wake of Major Ransomware Takedowns

In a remarkable demonstration of international cooperation, law enforcement agencies from across the globe have recently made significant strides against a notorious ransomware group known for its attacks on critical institutions in the United States, including hospitals and schools. This group, responsible for deploying the destructive Lockbit ransomware, has seen its operations severely disrupted. The […]
Open Letter: The Critical Importance of Cybersecurity in Protecting Your Business and the Greater Community

Dear Small Business Owners, In today’s digital age, the importance of cybersecurity cannot be overstated. As an IT services provider deeply committed to the security and prosperity of small and medium-sized businesses, WheelHouse IT is writing this to underscore a vital message: the digital threats facing large organizations, particularly in the healthcare sector, are a […]
Navigating the AI Threat Landscape: A Guide for Businesses from WheelHouse IT

In the rapidly evolving digital age, integrating Artificial Intelligence (AI) into our daily lives and business operations has been nothing short of revolutionary. With the advent of Large Language Models (LLMs) like OpenAI’s ChatGPT and the widespread adoption of generative AI, the promise of enhanced efficiency and creativity is undeniable. However, this technological leap forward […]
National Hurricane Center says no to adding Category 6 to Scale
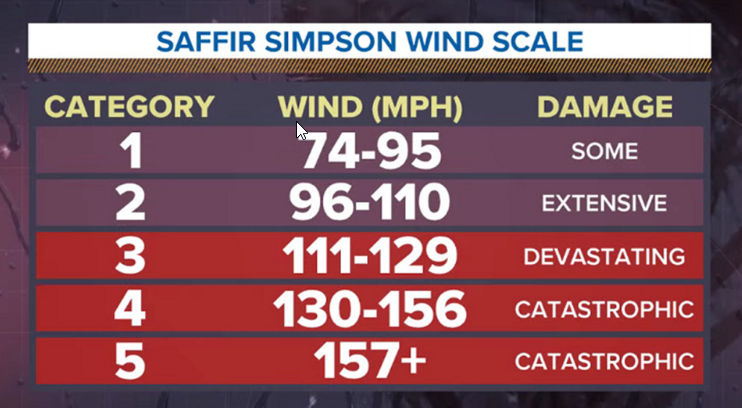
In recent discussions surrounding the intensification of tropical storms due to climate change, rumors swirled about a potential new addition to the hurricane scale: a Category 6. We even reported these rumors just two days ago. A study suggesting that the strongest storms are becoming even more powerful sparked this speculation, leading to debates on […]
Strengthening Business Continuity: Key Learnings from Hurricane Idalia for IT Preparedness

In the aftermath of Hurricane Idalia, a powerful reminder of nature’s force, WheelHouse IT underscores the vital need for businesses to bolster their storm preparedness, especially from an IT and technology perspective. The hurricane’s journey from a Category 4 intensity over open waters to making landfall as a Category 3 storm near Keaton Beach, FL, […]








