Migrating to the Cloud? Avoid These Problems

Cloud migration can often be a touchy situation. We’ll take a look at some problems you may face, and how to make sure they don’t weigh down your next cloud migration.
Tip of the Week: Outlook 2016 Can Do More than You Think
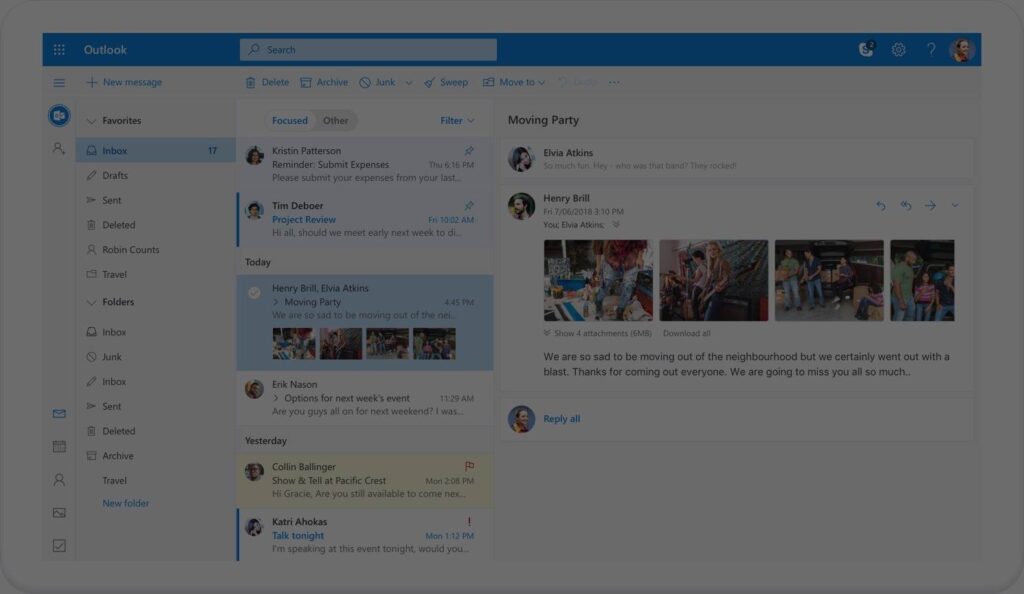
Email is one of the most common productivity tools in any office. It can also be one of the easiest to become disorganized. However, users of Microsoft Outlook 2016 will find that the program provides plenty of useful tools to ensure that your communications don’t get out of hand. For this week’s tip, we’ll explore […]
Cloud Resources: Stop Wasting Your Resources in the Cloud

The cloud is perhaps one of the single most important developments to happen to the modern workforce, changing the way that many organizations function and access cloud resources. Some use it for access to crucial applications that are needed to keep their businesses running, while others might use it to host critical parts of their […]
How Does the Cloud Help Businesses?

How does the cloud help businesses? Cloud computing has revolutionized the way that businesses approach operations, which brings about the question of how your organization can utilize it to further your earning potential and operational efficiency. That being said, how does the cloud help businesses? For businesses that are still not sure about implementing a […]
The Cloud Firewall: An Important Defense Against the Experienced Hacker

The Cloud Firewall Cyber criminals use a variety of techniques and tools to perform their “trade”, but the cloud firewall can stop them in their tracks. Successful hackers follow a well-developed organized process that usually consists of these five steps: Reconnaissance Scanning Gaining access Maintaining access Covering tracks This process parallels that used by a thief […]








