Beyond the Big Players: Why HIPAA Compliance Matters for All in Healthcare
As we forge ahead into 2024, the narrative surrounding cybersecurity within the healthcare sector is evolving. No longer are discussions about cyber threats and HIPAA compliance confined to the corridors of large hospitals and healthcare agencies. A recent wake-up call came from incidents involving smaller entities within the healthcare ecosystem, illustrating a critical point: cyber […]
Staying Vigilant in the Wake of Major Ransomware Takedowns

In a remarkable demonstration of international cooperation, law enforcement agencies from across the globe have recently made significant strides against a notorious ransomware group known for its attacks on critical institutions in the United States, including hospitals and schools. This group, responsible for deploying the destructive Lockbit ransomware, has seen its operations severely disrupted. The […]
Navigating HIPAA Compliance: Your Guide to Reporting Small Healthcare Data Breaches Before the Deadline

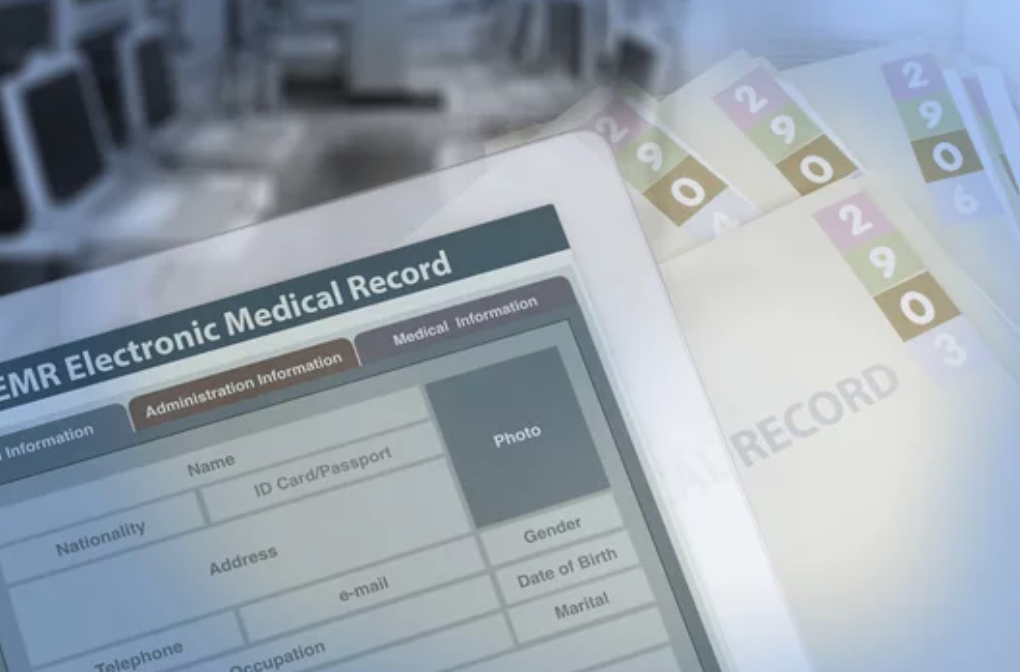
As we edge closer to the critical date of February 29, 2024, healthcare organizations are reminded of the looming deadline for reporting small healthcare data breaches, specifically those involving fewer than 500 records. This year, the calendar brings a slight twist with the leap year adjustment, setting the deadline a day earlier than the usual […]
Navigating the AI Threat Landscape: A Guide for Businesses from WheelHouse IT

In the rapidly evolving digital age, integrating Artificial Intelligence (AI) into our daily lives and business operations has been nothing short of revolutionary. With the advent of Large Language Models (LLMs) like OpenAI’s ChatGPT and the widespread adoption of generative AI, the promise of enhanced efficiency and creativity is undeniable. However, this technological leap forward […]
Addressing the Rising Threat of AI-Powered Cyberattacks

In a significant announcement, Microsoft has highlighted an emerging threat landscape where cybercriminals are leveraging ChatGPT, the advanced chatbot developed by OpenAI in November 2022, to orchestrate sophisticated cyberattacks. As a leading provider of comprehensive IT solutions, WheelHouse IT is closely monitoring these developments to ensure our clients’ digital environments remain secure against evolving threats. […]








